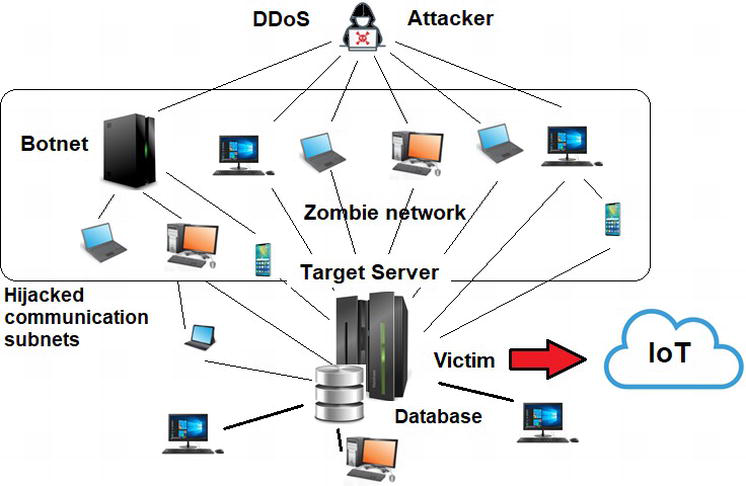
Internet of Things and Distributed Denial of Service as Risk Factors in Information Security | IntechOpen
SECURITY Question] DOS Attack / data flooding on bluetooth layer possible? · Issue #309 · corona-warn-app/cwa-documentation · GitHub
GitHub - crypt0b0y/BLUETOOTH-DOS-ATTACK-SCRIPT: Script for quick and easy DOS-attacks on bluetooth devices for pentest purposes