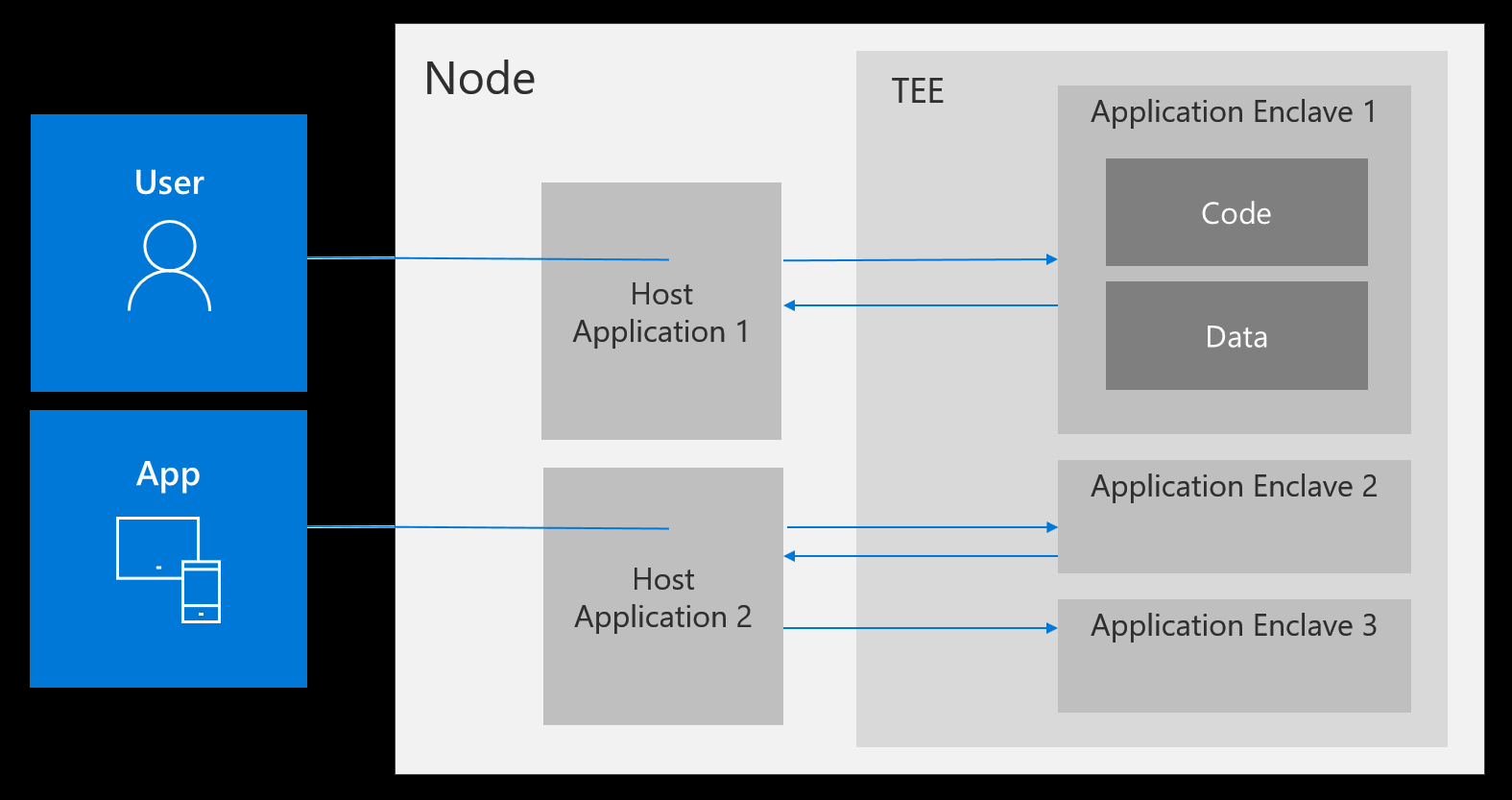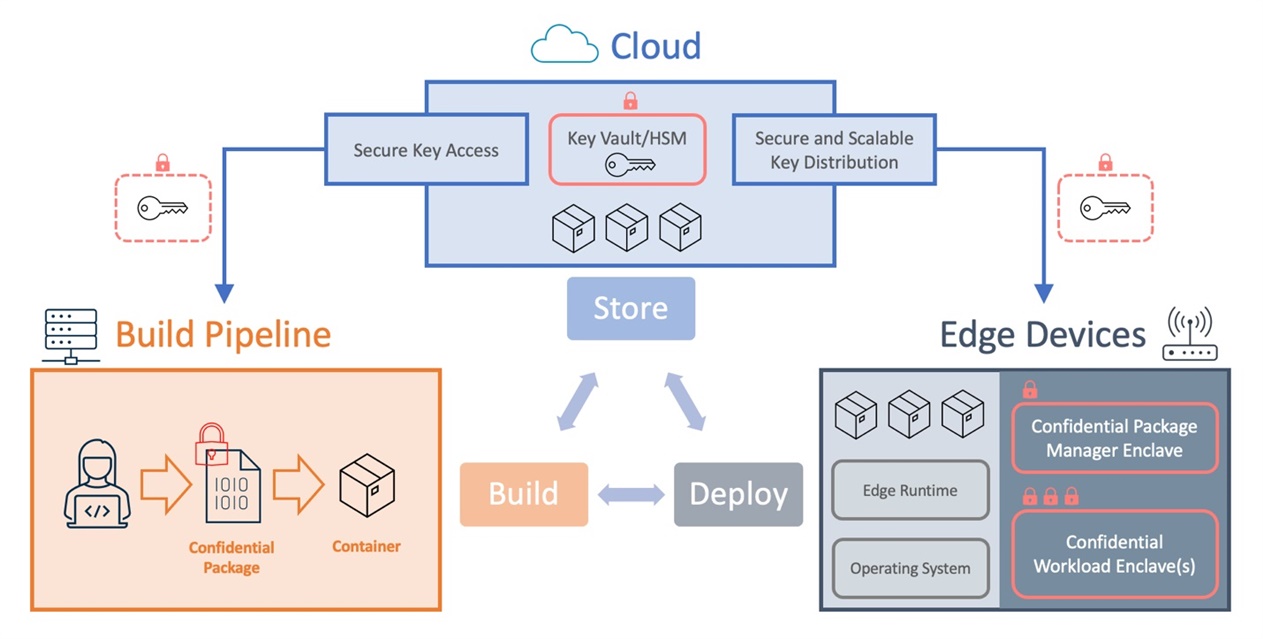
Confidential Computing Brings Secure Data Processing to the Edge - Infrastructure Solutions blog - Arm Community blogs - Arm Community

Oasis Labs joins the Confidential Computing Consortium | by Anne Fauvre-Willis | Oasis Labs | Medium

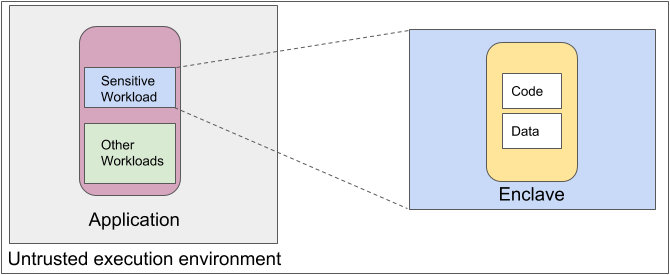
Confidential Computing and Machine Learning — Running TensorFlow Models Inside Secure Enclaves with Fortanix Runtime Encryption® | by Fortanix | Medium
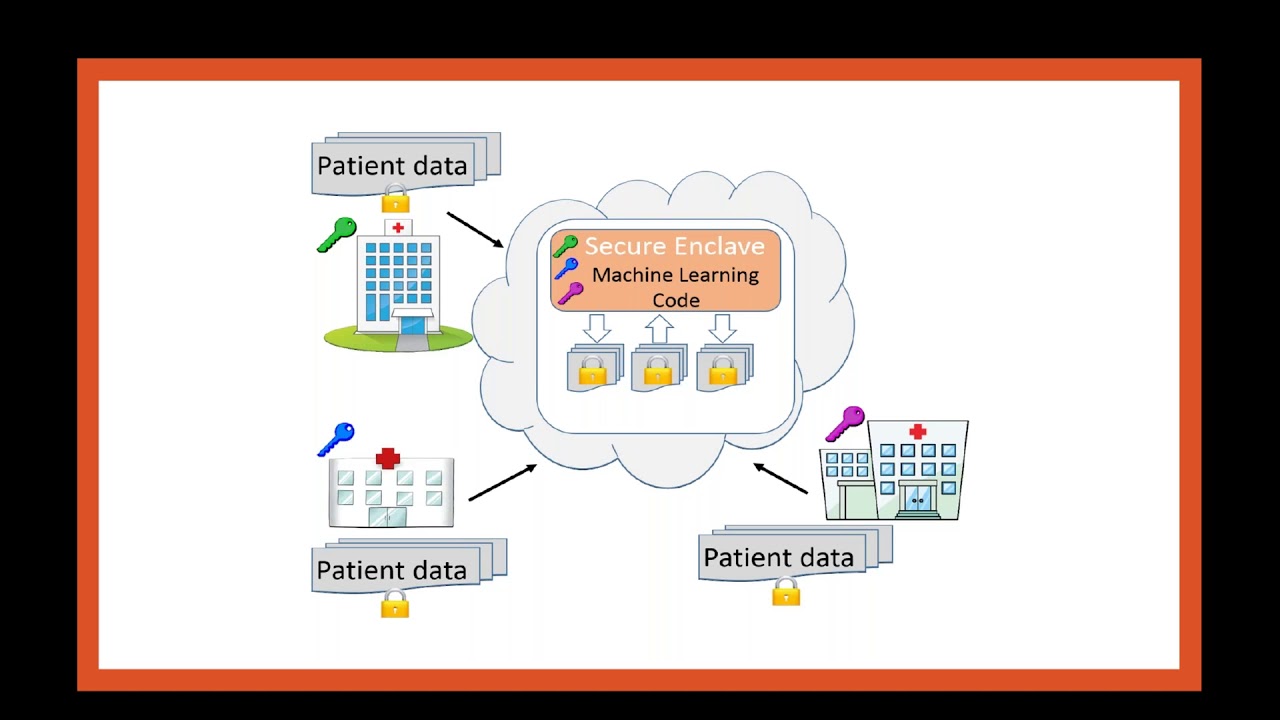
Secure Multiparty Machine Learning with Azure Confidential Computing - European SharePoint, Office 365 & Azure Conference, 2022

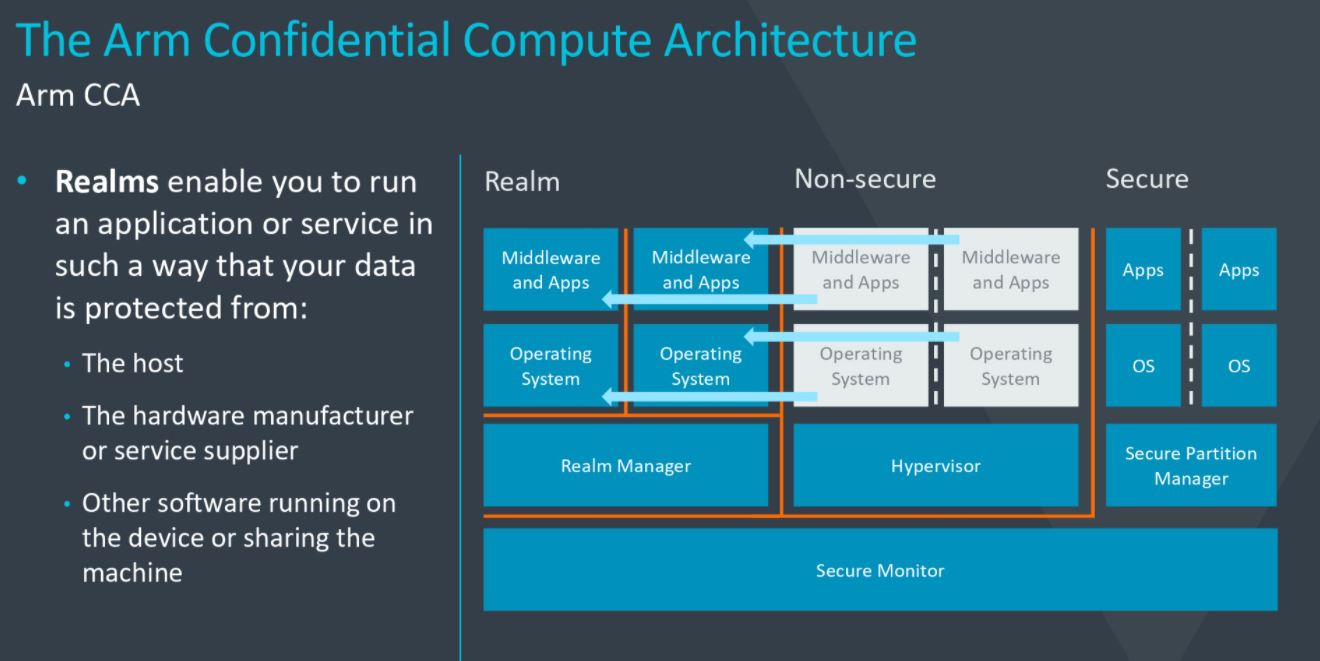
Introducing the Confidential Compute Architecture - Arm Announces Armv9 Architecture: SVE2, Security, and the Next Decade

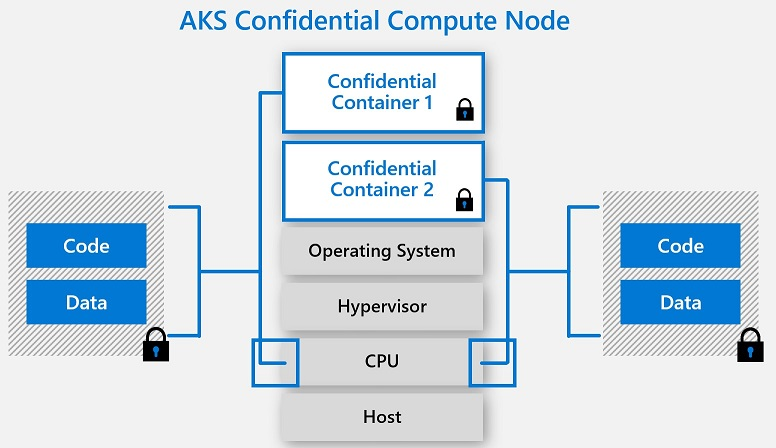
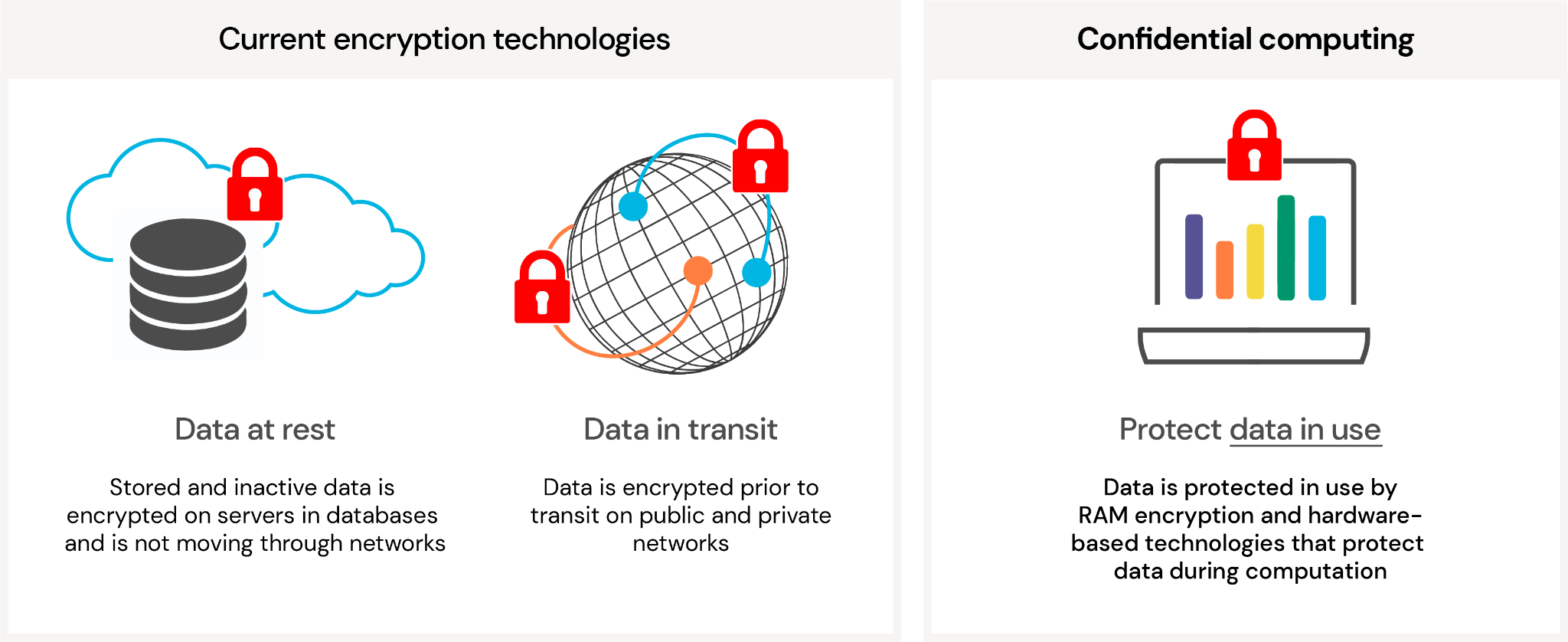
Navigating confidential computing across Azure - Dr. Ware Technology Services - Microsoft Silver Partner
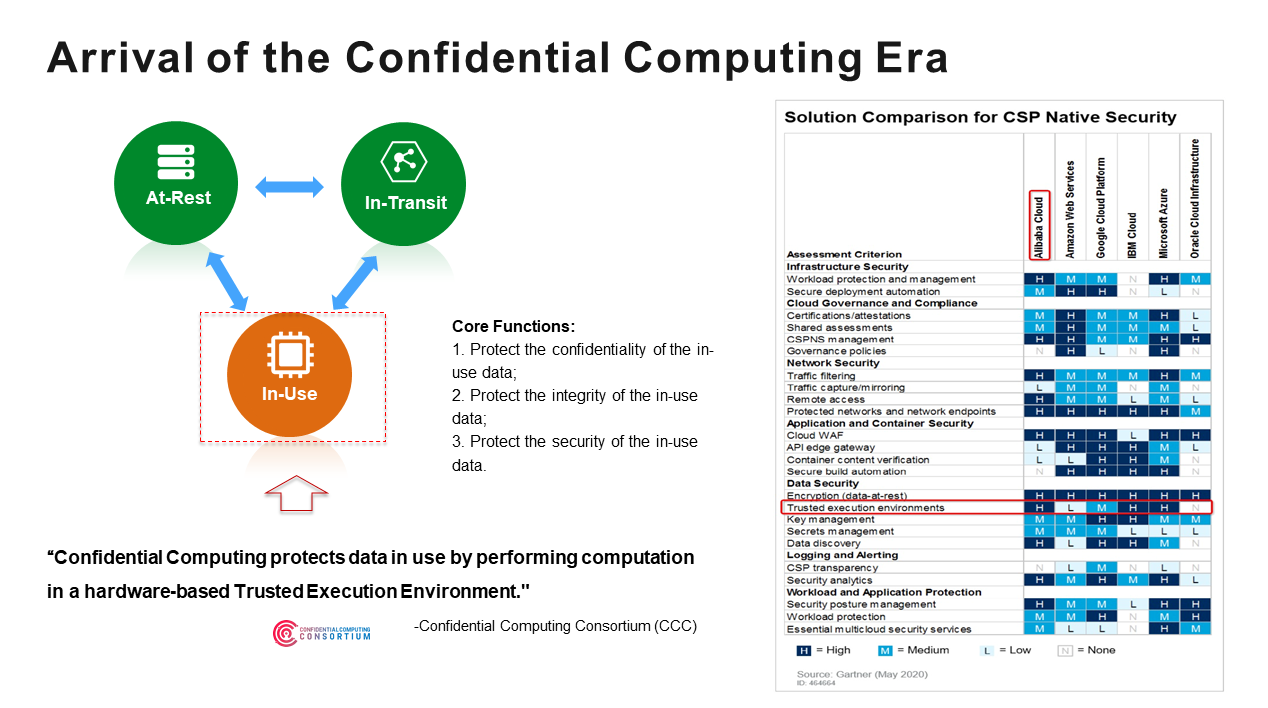
When Kubernetes Encounters Confidential Computing, How Does Alibaba Protect the Data in the Container? - Alibaba Cloud Community