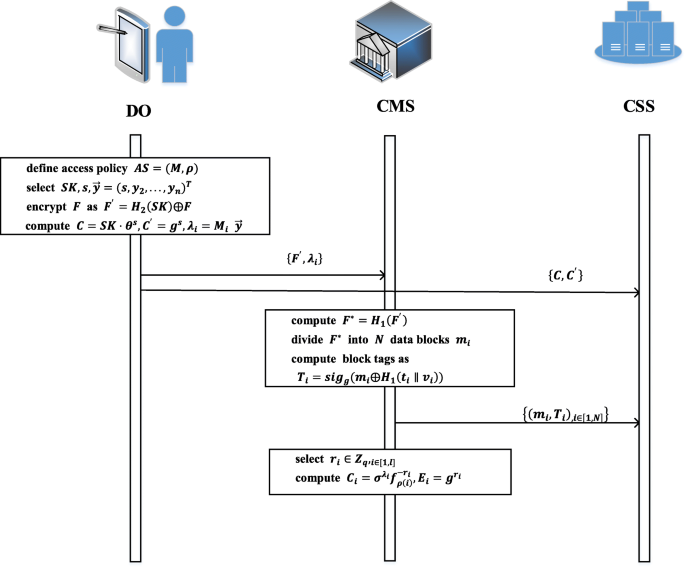
Sensors | Free Full-Text | A Secure and Lightweight Fine-Grained Data Sharing Scheme for Mobile Cloud Computing

PDF) An Advanced Mechanism for Secure Data Sharing in Cloud Computing using Revocable Storage Identity Based Encryption | AIPublications Journals - Academia.edu

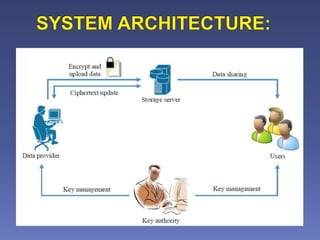
A novel system architecture for secure authentication and data sharing in cloud enabled Big Data Environment - ScienceDirect
![PDF] SECURE DATA SHARING IN A CLOUD ENVIRONMENT BY USING BIOMETRIC LEAKAGE-RESILIENT AUTHENTICATED KEY EXCHANGE | Semantic Scholar PDF] SECURE DATA SHARING IN A CLOUD ENVIRONMENT BY USING BIOMETRIC LEAKAGE-RESILIENT AUTHENTICATED KEY EXCHANGE | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/651dac40537dd4b2bf4b3f46168c9a808a1acddf/3-Figure1-1.png)
PDF] SECURE DATA SHARING IN A CLOUD ENVIRONMENT BY USING BIOMETRIC LEAKAGE-RESILIENT AUTHENTICATED KEY EXCHANGE | Semantic Scholar
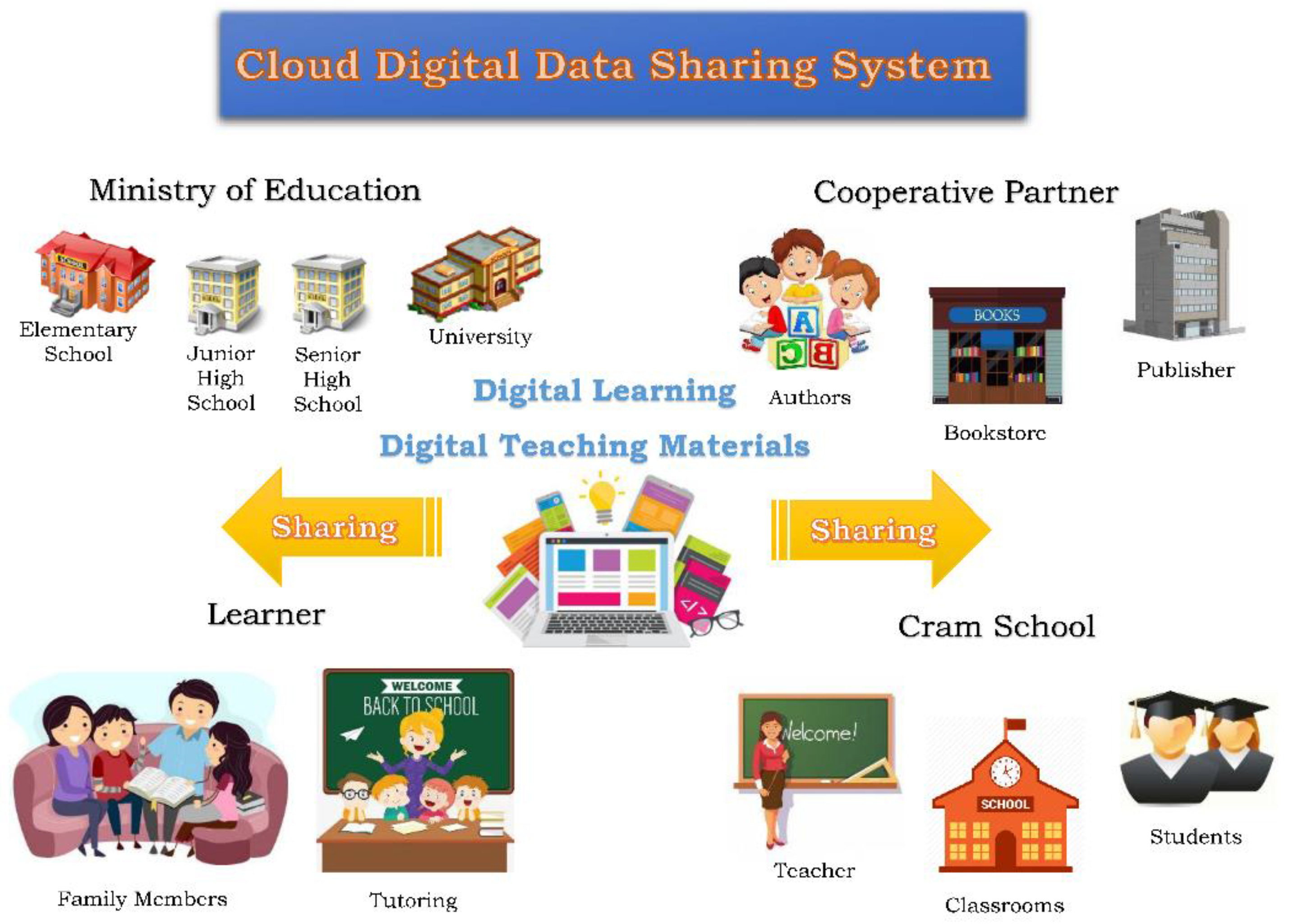
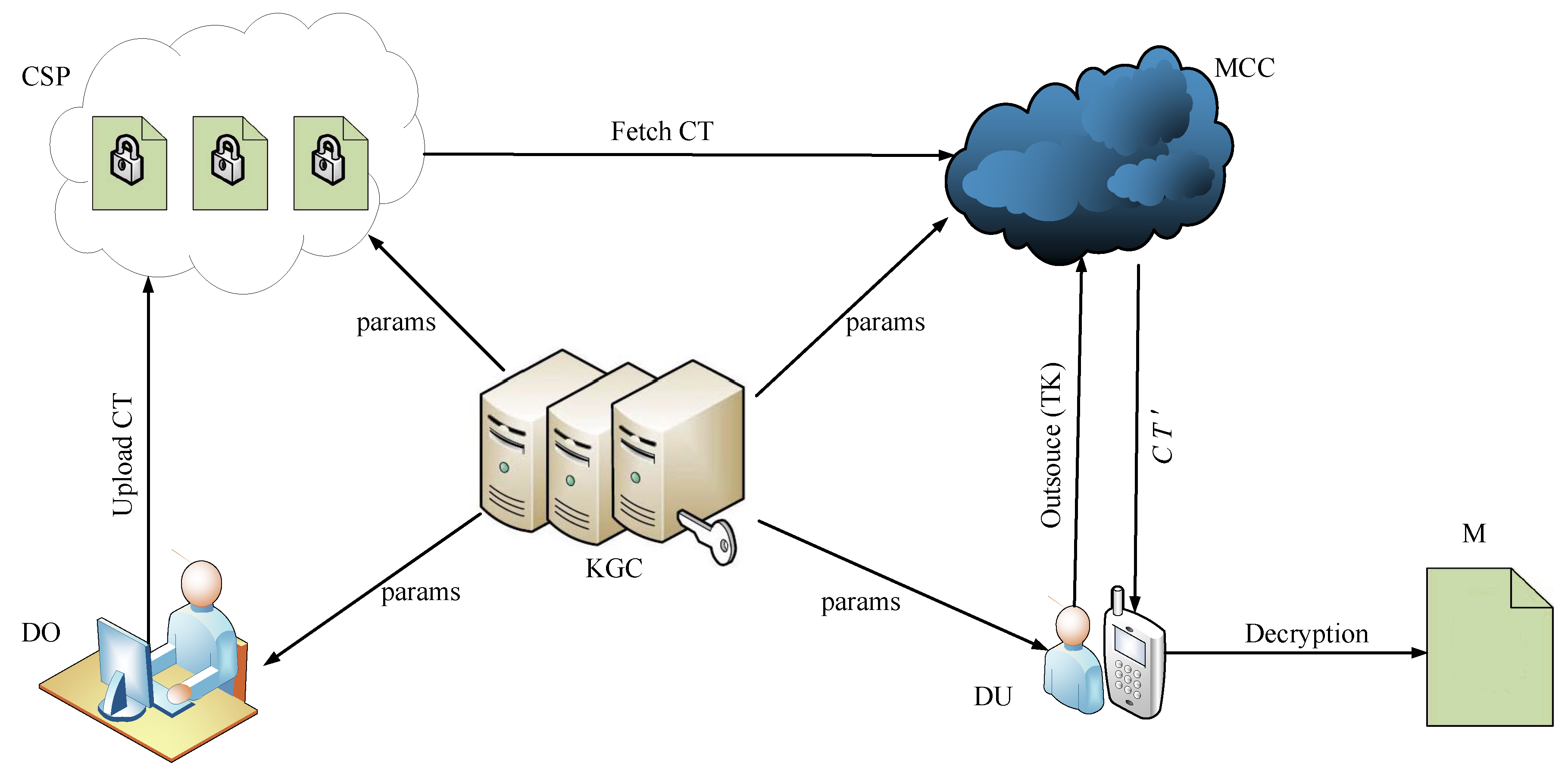
Sensors | Free Full-Text | A Secure and Efficient Digital-Data-Sharing System for Cloud Environments
Cloud Computing Vector Icons Set: Data Storage, Cloud Security, Data Sharing, Cloud Database, File Synchronization, Authorization, Server, Statistics, Data Safety. Modern Line Style Royalty Free SVG, Cliparts, Vectors, And Stock Illustration. Image
Cloud computing and internet technology, database remote access. Web hosting, online services data protection. Information security, data sharing and backup. Thin line icons set. Vector illustration Stock-Vektorgrafik | Adobe Stock
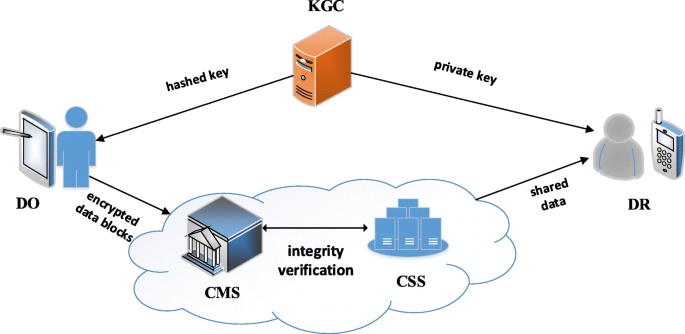
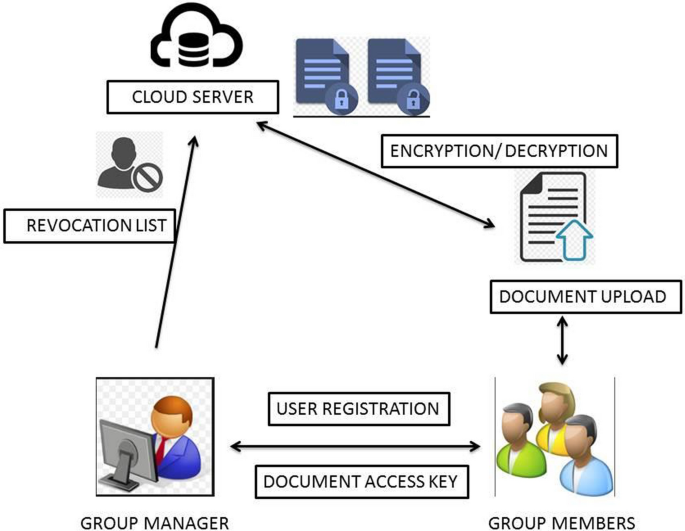
An efficient and secure data sharing scheme for mobile devices in cloud computing | Journal of Cloud Computing | Full Text
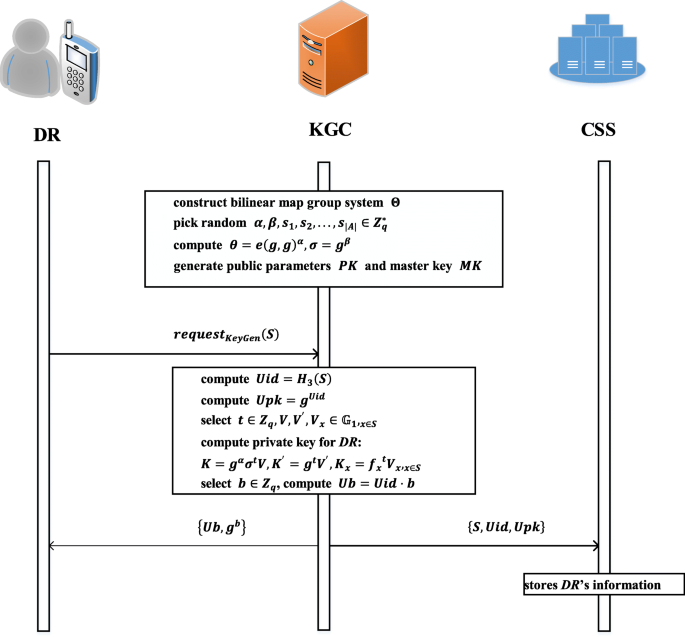
An efficient and secure data sharing scheme for mobile devices in cloud computing | Journal of Cloud Computing | Full Text