SharpHound (v1.4) crashes/exits on Win 10 Enterprise (1709) 64-bit · Issue #137 · BloodHoundAD/BloodHound · GitHub
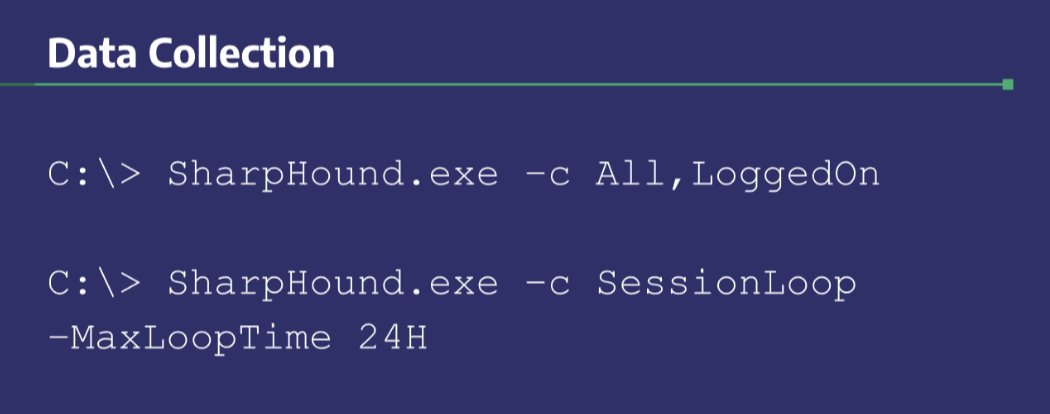
Jeff McJunkin on Twitter: "tl;dr for BloodHound data collection: SharpHound.exe -c All,LoggedOn SharpHound.exe -c SessionLoop -MaxLoopTime 24H It's sadly possible for this dual-use tool to be flagged as malicious by AV. Easy
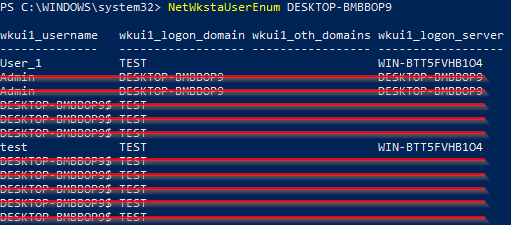
BloodHound Inner Workings & Limitations – Part 2: Session Enumeration Through NetWkstaUserEnum & NetSessionEnum – Compass Security Blog

Stopping Active Directory attacks and other post-exploitation behavior with AMSI and machine learning - Microsoft Security Blog

Post-Exploitation Basics In Active Directory Environment By Hashar Mujahid | by Hashar Mujahid | Aug, 2022 | InfoSec Write-ups